Apr 30, 2023
Discovering the Hidden Depths of the Dark Web with Tor

As a result, users may regularly be exposed to various types of malware such as Keyloggers, Botnet Malware, Ransomware, and Phishing Malware. If you decide to continue exploring any dark web site, you put yourself at risk. Download Tor Browser. Other Browsers. Tor Browser is the easiest alternative to access the Deep Web, but it is not the only one. Was this content helpful?
When accessing a search engine and performing a query, it does not scan the entirety of the Internet for results, but instead only searches within its own database. It is well known that cybercriminals investigate and exploit these platforms. To enter the Deep Web, simply execute the installer and follow the on-screen instructions.
This is because, instead of directly accessing the server of the target site, your computer will connect to a Tor machine, which will then connect to another machine, which will connect to another machine and so on, like a tunnel. We finish the review of darknets with I2P. Intranets: internal networks of companies, governments and educational facilities used to communicate and control private aspects within their organizations.
Over time, the platform has been redefined and has since become public in the form of the browser we know today.
Understanding the Differences Between Dark Web and Deep Web
Meta-proxy encryption, file system encryption, and sandbox isolation for applications are just a few of the security measures used to access the Deep Web. In reality, when we talk about the Dark Web or Darknet, we are referring to various networks that overlay the public internet and require specific software, configurations, or authorization to access. Tails comes equipped with all the necessary tools to connect to the Deep Web.
Before making any purchases, acquire unidentifiable prepaid debit cards for entering the Deep Web.
How to access? It can be said that the dark web is a collection of networks and technologies used to share information and digital content.
Diving into the Depths of the Dark Web
There may even be certain content that you won't be able to access even if you want to because they have an extra layer of protection to prevent just anyone from accessing them, but it's most likely that you won't even see them. Make sure to take advantage of these tools if you have them at your disposal.
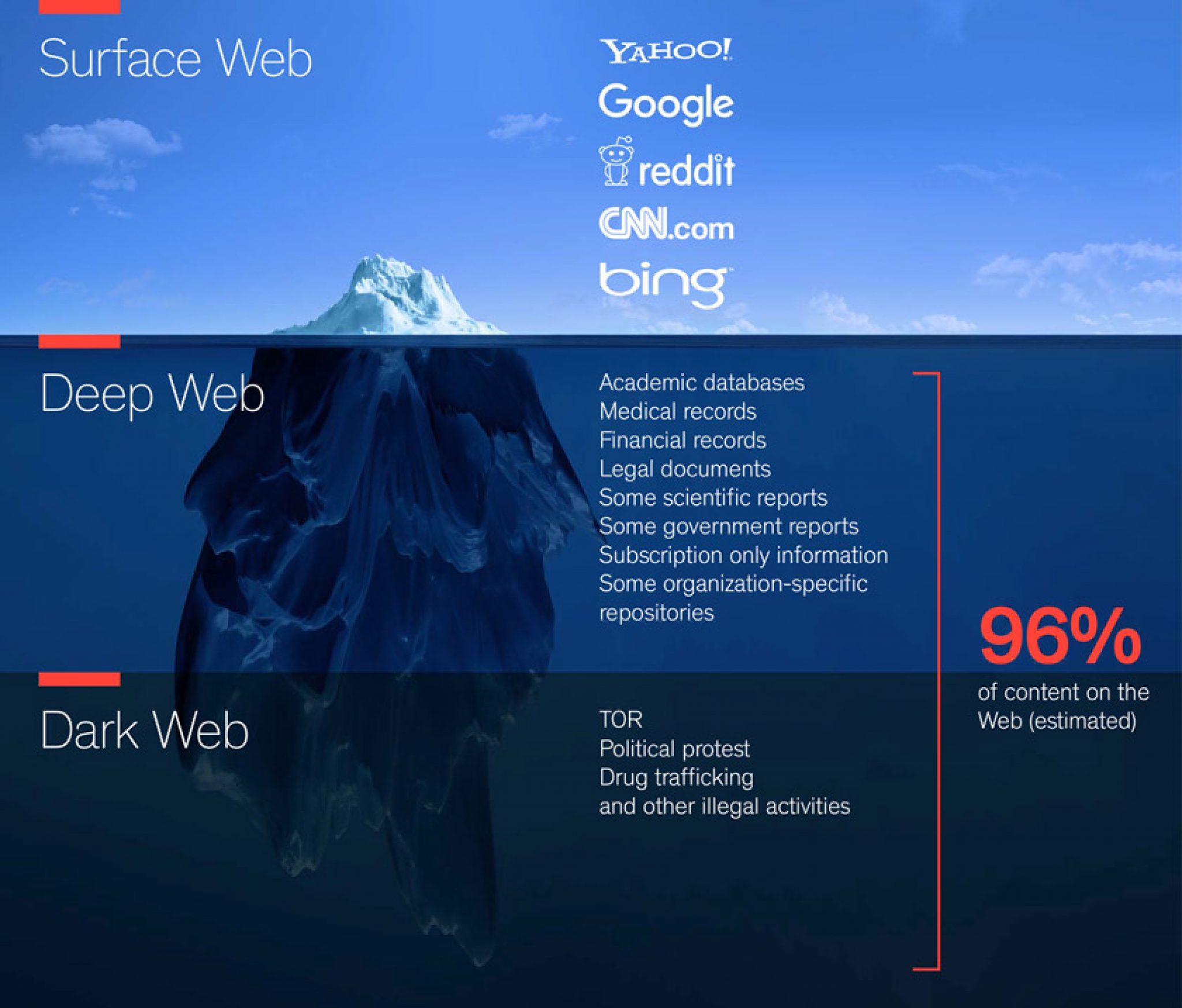
For instance, if a user leverages the Deep Web to commit fraud, identity theft, hacking, or any other illegal activities, they may be violating the law and could face criminal charges. By using our ocean and an iceberg as an analogy, the dark web would be the submerged lower tip of the iceberg. Here are seven tips for safely accessing the dark web: Trust your intuition.
Entering the Deep Web
When entering the Deep Web, one should be aware of the potential risks that come along with it. It is not uncommon to come across a multitude of malware and advertisements while browsing. However, the installation process is quite simple and once completed, Freenet will open with our preferred browser.
For those who require a more secure way of working with the Deep Web, Subgraph OS and Tails OS are highly recommended. In particular, Tails OS is a system specifically designed for this purpose and offers a tailored approach to ensure maximum safety.
Start browsing Now you can access any valid site on the deep web.
Furthermore, additional measures of connection and traffic protection are sometimes required to access certain sites on the dark web. Definition of the Dark Web The Dark Web is the hidden collection of Internet sites that can only be accessed through a specialized web browser.
Diving into the Depths of the Dark Web: An Introduction to Hidden Websites
In this way, you will not put your device's integrity at risk nor compromise your personal deep web entrar information. Any online activity can leave traces back to your identity if someone investigates thoroughly enough. Several reports have suggested that the dark web offers many illegal services, from paid assassinations to sex and arms trafficking.
There are two types of deep web, P2P or peer-to-peer such as Freenet, i2p, GNUnet, Entropy, ANts P2P, and non-P2P like Tor. Confidential HIPAA information, such as medical documentation, is found here. Criminals in the depths: While it is true that there are many curious or digital crime investigators on the deep web, you could also come across a hacker who is adept at tracking.
Explore further
Distributed by scotty, LLC.