May 06, 2023
Mastering the Dark Web: A Guide to Purchasing Stolen Credit Cards via Tor

Despite its popularity for accessing the dark web, Tor has some vulnerabilities that can compromise its users' anonymity. For instance, the Tor Browser is built on the Mozilla Firefox platform, making it vulnerable to similar attacks as other browsers. Additionally, recent reports suggest that search engines still have a long way to go in improving their ability to accurately report Tor-related activities. Nevertheless, Tor remains a popular choice for those seeking to access the dark web as it provides a layer of privacy and security that other browsers cannot match.
Dispose of the Tor Browser application by dragging and dropping it to the Trash. Upon launching the Tor Browser, a prompt will appear, inquiring if you desire to connect to Tor. The Tor network utilizes multi-layered encryption to ensure your traffic is relayed and encrypted three times.
If you want to ensure top-notch protection, the most effective solution is to merge Tor with a VPN. However, it's important to keep in mind that this may result in slower service.
Navigating the Dark Web: A Guide to Accessing Tor
If you intend to use Tor for accessing the dark web, you should be prepared for slower speeds due to the encryption and decryption of your traffic as it passes through various relays. To ensure enhanced protection for all your online activities, it is highly recommended to use a Virtual Private Network in conjunction with Tor. Nevertheless, the Dark Web can serve legitimate purposes like providing anonymity to whistleblowers and journalists.
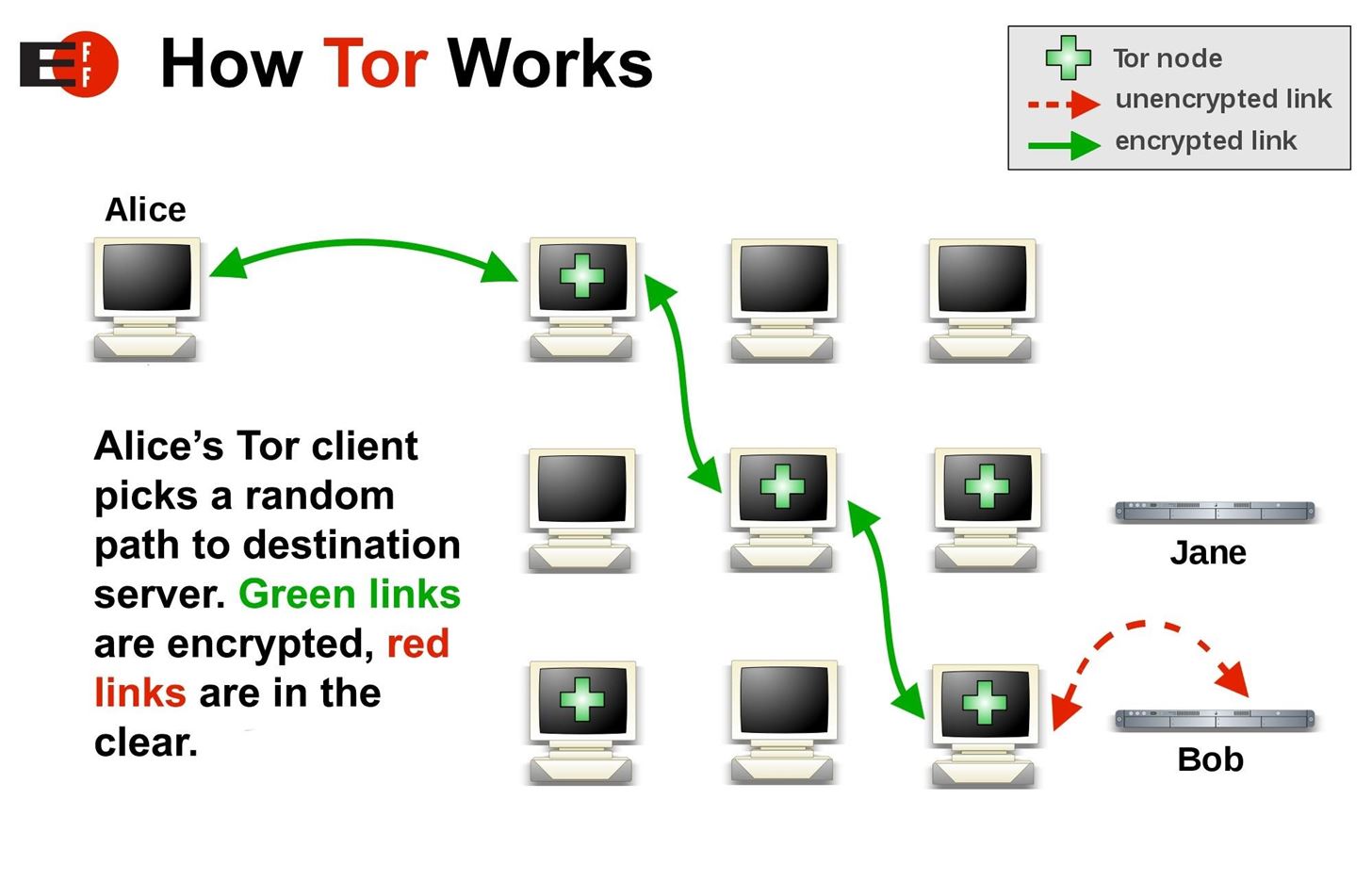
Tor, which stands for The Onion Router, is a free and open-source software that allows users to access the internet anonymously. It is mainly used to access the dark web, which is a part of the internet that is not indexed by search engines and is often associated with illegal activities. Tor works by routing a user's internet traffic through a series of servers, making it difficult for anyone to trace the user's activities back to their computer. Tor also encrypts the user's internet traffic, ensuring that their online activities remain private. While Tor is a valuable tool for those who value their privacy online, it is important to note that it can also be used for illegal activities. As such, it is important to use Tor responsibly and to be aware of the potential risks involved.
Dark web users often utilize Tor, a network that allows for anonymous communication and browsing. To use Tor, users must download the Tor Browser Bundle, which includes the necessary software to access the network. In addition, the bundle also comes with the NoScript and https Everywhere extensions, adding an tor for dark web extra layer of protection. To install the Tor Browser, simply drag the icon onto the Applications folder icon.
Discovering the Dark Web with Tor: A Guide
When it comes to accessing the Dark Web, Tor is a popular choice. Unlike other live OS options that require a USB stick to boot from, Tor uses multiple layers that are peeled off as you travel from server to server. However, there are still live OS options available such as Subgraph OS, Freepto, and Tails, which can be run on almost any computer by simply inserting a USB stick and booting from it.
When it comes to accessing the dark web, Tor is a popular technology that is unlikely to result in any legal issues in most countries (although good luck navigating through the murky waters of the dark web). However, it is worth noting that using Tor can be quite processor-intensive and slow, so users should be prepared for a potentially slower browsing experience.
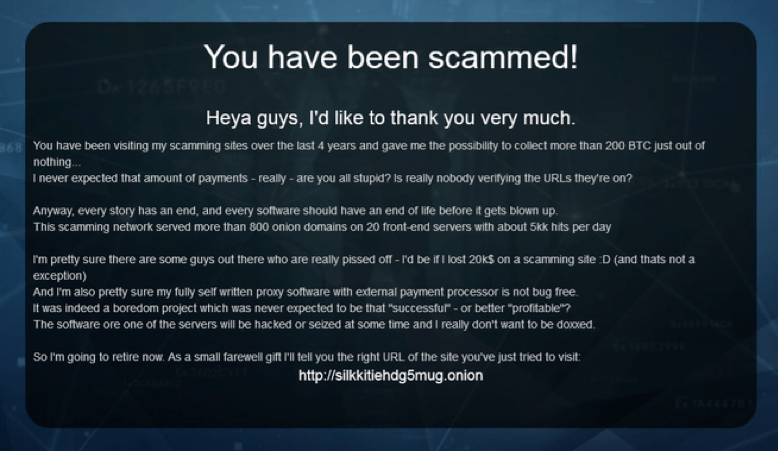
The purpose of Tor for the dark web is to remove a layer of encryption and transmit data to the next relay. The opinions expressed in this article are solely the responsibility of TechRadar Pro and do not represent any other entity.
The use of Tor for accessing the dark web has been a hot topic in recent years. Tor, short for The Onion Router, is a free and open-source software that allows users to browse the internet anonymously. It does this by routing your internet traffic through a series of nodes, making it difficult to track your online activity.
However, it is important to note that while Tor provides anonymity, it is not foolproof. There are certain things you should avoid doing while using Tor to ensure your online safety. For instance, you should not use your real name or personal information while creating accounts on the dark web. Additionally, you should not download any suspicious files or click on any links from untrusted sources.
The CISA has published a list of free cybersecurity tools and services that can help you stay safe while using Tor. One such tool is the Underactor, which can reveal pixelated text to expose sensitive data. It is also crucial to keep your software up-to-date and to use a reputable antivirus program.
If you are interested in accessing the dark web using Tor, it is important to keep in mind that your internet speeds may be slower than usual due to the encryption of your traffic. The dark web is a part of the internet that is not accessible through standard web browsers, and can only be accessed using special software like Tor.
In conclusion, while Tor provides anonymity and access to the dark web, it is important to use it responsibly and take necessary precautions to ensure your online safety.
Accessing the Dark Web with Tor: A Comprehensive Guide
When it comes to accessing the tor for dark web dark web and maintaining anonymity, Tor is the go-to tool for many. However, another option that has a proven track record for anonymity is DuckDuckGo. In fact, the privacy advocate team behind DuckDuckGo has been known for a long time as a staunch opponent of Google. To access Tor for dark web browsing, simply find the Specialty server category.
If you want to change the exit node in Tor Browser, follow these steps: locate the Tor Browser folder on your main Desktop page. However, despite its effectiveness in safeguarding your privacy and anonymity, using Tor Browser as your primary browser is not recommended. As for which search engine to use for the Dark Web, there are several options available.
Explore further
Distributed by onetoughbabe23_2007, LLC.